Abstract: This report examines the concept of brainwallets and in which contexts they may be useful. As an experiment eight Bitcoin private keys were created, using passphrases from popular works of fiction and other media. All the funds were swept away in a short amount of time and in one case, remarkably, the funds were taken in around 0.67 seconds. The report concludes by arguing that brainwallets may not be a safe way to store coins, certainly not by using popular phrases in published works.

Overview
Unfortunately humanity is often plagued by refugee crises, from WW2 to more relatively recent conflicts in regions such as Syria, Yugoslavia or Afghanistan. In these scenarios families often need to quickly flee a region to reach safety, leaving behind their belongings. Like many readers of this report, I personally know this all to well, just two generations ago my jewish relatives resided in Nazi Germany prior to the outbreak of WW2 and they fled the country to seek refuge in the UK. My relatives had substantial wealth at the time, however it could not be transported effectively and when they arrived in the UK they had nothing to their names. With the benefit of hindsight, leaving their wealth behind in Germany was not a significant problem and my family is lucky to have survived. Of course, one can try to carry gold or diamonds on your journey, but there is always the risk of search and seizure, especially when crossing a hostile border.
This is when Bitcoin advocates step into the argument, claiming that Bitcoin is a potential solution to this problem facing refugees and others afraid of wealth confiscation. One can use a “brainwallet”. Refugees need to carry nothing with them, all they would need to do is remember a Bitcoin wallet passphrase. Funds, potentially millions of US dollars, can therefore be effectively stored inside of one’s mind.
sha256(Call me Ishmael)=a88910233e176ef4489b52d686f326d7ff9ccff686065a44cbd3665384508ad6
A brainwallet user could choose a popular phrase, take the sha256 hash of it and then use that as the private key to generate a Bitcoin address. In this short report, as an experiment, I generated some brainwallets and examined their security characteristics.
Brainwallet experiment
The below table displays eight brainwallets I generated, from popular works of fiction, musical lyrics or academic literature. None of the wallets have been used before in Bitcoin’s history as I generated eight new unused addresses. In one transaction, I then sent 0.005 BTC to each address. I am interested in assessing the viability of brainwallets and whether and how quickly the funds may be swept away, by hackers able to guess the passphrase I chose.
| Passphrase | Source | Sha256 | Type | Address |
| Call me Ishmael | “Moby-Dick” by Herman Melville |
a88910233e176ef4489b 52d686f326d7ff9ccff6 86065a44cbd366538450 8ad6 |
Compressed |
121qcemzF3HHsvhggufE XNedHncAzzT41T |
| Uncompressed |
168z2uEg5Shzsgknq561 oefN2xmLpjZUvH |
|||
| It is a truth universally acknowledged, that a single man in possession of a good fortune, must be in want of a wife | “Pride and Prejudice” by Jane Austen |
be09c4df6444afa6adff 8098c0cf273c3e9fef04 a1a8e20de8218eca0bec 383d |
Compressed |
17N4w1bMcfU6XCYABVwh EyJSW8bjkZX1Wr |
| Uncompressed |
1PuZXtWfXRdBzFcQ9ARuL 7D8ydnfmhQKzF |
|||
| It was the best of times, it was the worst of times, it was the age of wisdom, it was the age of foolishness, it was the epoch of belief, it was the epoch of incredulity, it was the season of Light, it was the season of Darkness, it was the spring of hope, it was the winter of despair | “A Tale of Two Cities” by Charles Dickens |
e051a4337000945d99a4 6ac1b56244106f732535 c11c22c229c6d620ab47 199f |
Compressed |
1DMowSp8G1v5bFyfV4R DFcPRERfcqycWVx |
| In the beginning God created the heaven and the earth | The King James version of the Bible |
f153b22c61d6013bf2d7 aa5a3fe7532718763613 1e9022dab1304333751a 7301 |
Compressed |
1EsxEASH5tSHGzmKohT FNBGr9xAcyTawyL |
| The answer, my friend, is blowin’ in the wind | “Blowin’ in the Wind” by Bob Dylan |
aeac73098d2b9a29ba47 c4893c2d0b6fbbba487d 21b1b3a57a55ee11c7a6 a476 |
Compressed |
175hVojnUG3P652wxMog VvzdAx2yFAo4q5 |
| The network is robust in its unstructured simplicity | Bitcoin Whitepaper by Satoshi Nakamoto |
1ecbe1b2d3242ee7b31e acc5aa2e382b19a8f937 825c2fac012221fdc0c4 9f35 |
Compressed |
19bHzxnvf8RFcjSCZsx1 TDREbEAryYYbRJ |
Sweeping of the funds
All the funds were swept away within a day and the 0.04 BTC I spent on this exercise were lost, potentially forever. Remarkably, three of the deposits were swept away before our transaction even got confirmed into the blockchain. In one case, an independently run Bitcoin node witnessed the transaction sweeping away funds occur just 0.670 seconds after it saw the original transaction enter its memory pool. This extremely fast sweep applied to the address with the passphrase “Call me Ishmael”, the opening line from the novel Moby-Dick.
Speed the brainwallet funds were swept away (Seconds)
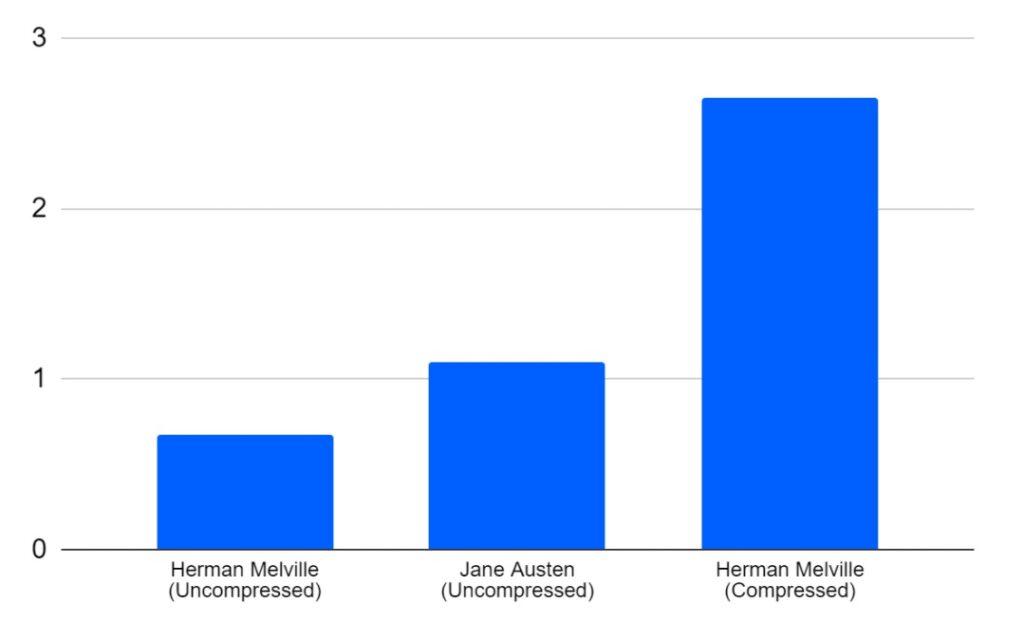
(Source: BitMEX Research)
(Notes: Timings based on when the transaction entered the memory pool of one of our nodes unrelated to this exercise)
The table below shows how fast the remaining funds were swept away. Four of the sweeps occurred after 22 blocks and all these sweeps appear to have been conducted by the same entity, as all four UTXOs were used as inputs in the same transaction. The final sweep, which contained text from the Bitcoin whitepaper, took 80 blocks.
Speed the brainwallet funds were swept away (Blocks)
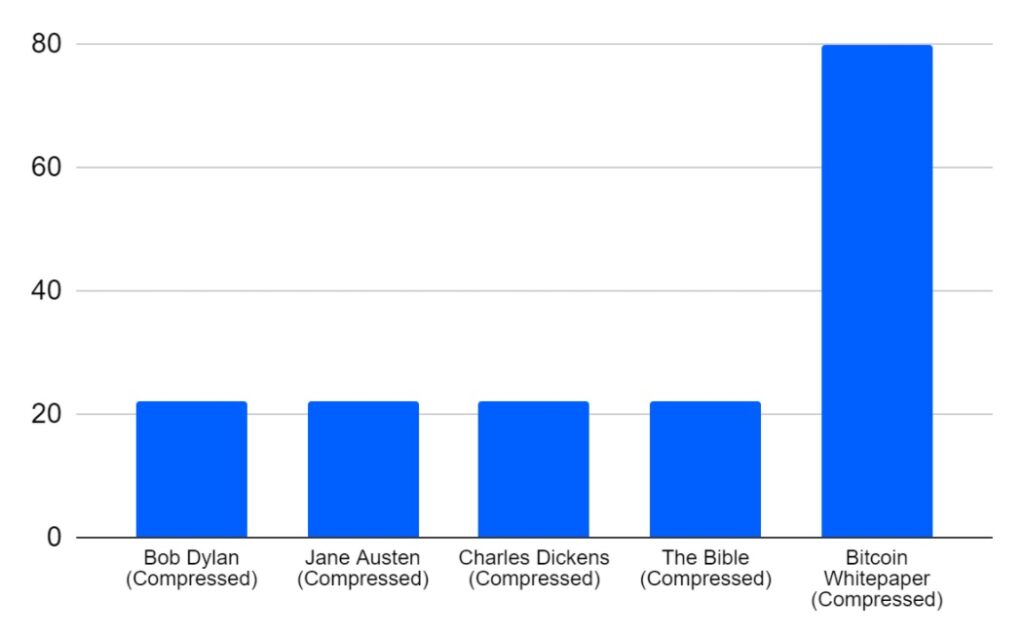
(Source: BitMEX Research)
(Notes: The first four sweeps all occurred in the same transaction)
Transaction fees
The sweep transactions tended to have very high fees, for instance the uncompressed “Call me Ishmael” sweep used a fee rate of 390 satoshis per virtual byte, several orders of magnitude above the prevailing market rate. This indicates that the hacker is in a race with other hackers and perhaps the legitimate coin owner, to get their transaction confirmed in the blockchain first. Indeed, this is a scenario where at least two entities know the private key and a higher transaction fee can increase the probability of a successful transaction.
Implications of the analysis
The speed and nature of the redemption of the funds clearly indicates that people have servers up online 24/7 scanning the blockchain and their respective memory pool’s for weak brainwallets to hack. These servers are likely to have pre-generated many hundreds of thousands of Bitcoin addresses, using text from thousands of published works, music, books, academic papers, magazines, blogs, tweets and other media and then stored these in a database.
Around a year ago, I conducted a similar experiment, where funds were sent to addresses generated by a reasonably obvious pattern deep inside some of the world’s best selling novels. These funds are still sitting in the blockchain today and have not been stolen. The key difference appears to be that these passphrases were not directly generated from unmodified text in the books, therefore the funds sit there unredeemed and the hackers have not yet found the passphrases. However, one should absolutely not consider this a safe way of storing funds.
As for where the eight outputs stolen from me ended up, at the time of writing, six went to new unused addresses and the coins have not been spent, while one went to a used address and the coins have also not been spent. Only one of the outputs has been spent, the coins sent to “The network is robust in its unstructured simplicity” address. Based on our very basic analysis, which could be incorrect, these coins appear to have been sent to HitBtc.
Conclusion
A basic conclusion here is simple, do NOT use a brainwallet from published materials, they are not safe. In a real world scenario, if someone (including a refugee) has access to Bitcoin, they probably also have access to the internet and therefore a more secure way of storing coins could be to email yourself an encrypted backup of your private key. Then the funds are stored online and you are not at risk of being searched. The encryption passphrase here will not instantly be subject to the attack with the large database of materials, however this could be a risk in the longer term if the email is compromised.
The above being said, if one knows what they are doing and has a strong understanding of the risks involved and how the attackers operate, it may be safe to use a brainwallet to a limited extent. For instance by combining sections of text from multiple works of fiction with birthdays in your family, your telephone number and at least one soure of randomness (e.g. dice). Please do not treat this example as advice, but the point is by combining many different categories of information, a secure brainwallet may be possible.
However, if you need to use a brainwallet, based on the data on this report, don’t choose anything simple or poetic. I found out the hard way.
Related
The post appeared first on Blog BitMex






