Chief Security Officer at cryptocurrency exchange Kraken, Nicholas J. Percoco alerted users today about a scam that was targeting crypto users, which involved a homograph phishing attack and “multiple” people who were pretending to be Kraken employees.
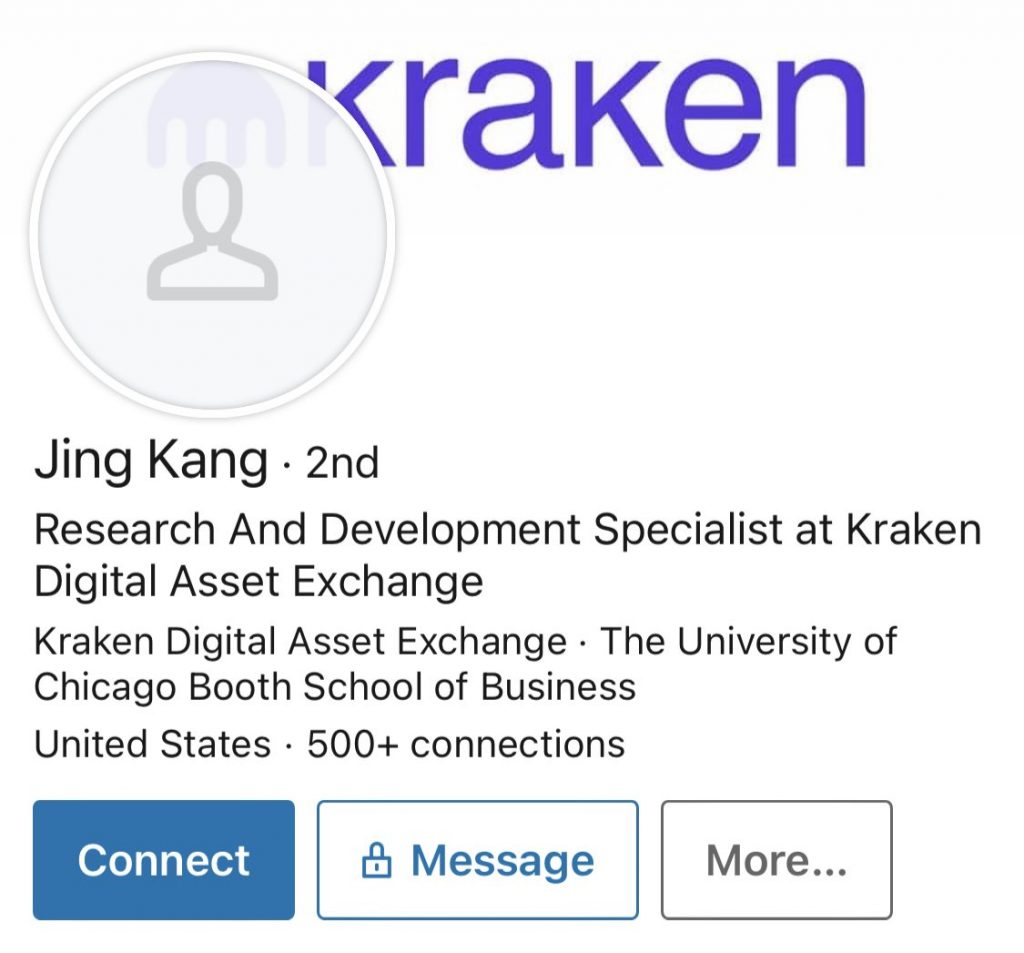
Percoco further alleged that people named Liz Cohen, Darin Zumberi or Jing Kang were posing as Kraken employees and that these “fake identities” were contacting Kraken users through telegram and LinkedIn. Percoco said in a tweet:
There is a scam that is targeting the cryptocurrency community and is very active right now […] If you were contacted by Liz Cohen, Darin Zumberi or Jing Kang – these are NOT Kraken employees, but rather puppet accounts used by the scammers.
The Chief Security Officer also shared screenshots of the alleged scam account from LinkedIn and the message these individuals had sent to an unnamed user:
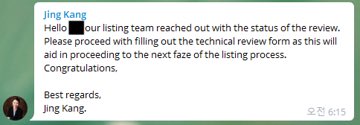
Percoco further claimed these scam operators made contact with users by also sending an email claiming to be part of Kraken’s listing team. According to the Chief, the alleged scammers would “follow up with an email’ and request the message seen in the below image:
These emails are said to be sent from a Punycode domain that according to Percoco “looks somewhat legit.” However, he noted a difference in the domain address’ font and stated that “these are not the Ks you’re looking for.” Note the font difference below:
Punycode domain allows people to convert words to look similar to other characters, which hackers often misuse to launch homograph attacks. While the URL looks legitimate, seen in the image above, it misleads users by redirecting them to a different website which is a common practice in phishing, forced downloads, and scams.
Most often web browsers use the “xn-- prefix” to indicate that the domain uses Punycode to represent other characters, and according to Percoco, looking out for the xn prefix protects users against such Homograph phishing attacks.
The post appeared first on AMBCrypto