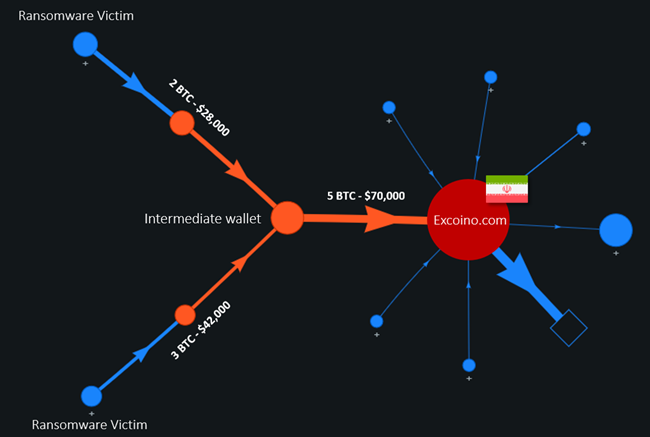
American-Israeli cybersecurity firm Check Point published a follow-up article that revealed the origin of Bitcoin ransomware that attacked several companies in Israel in the last couple of weeks. Check Point researchers partnered with Whitestream – a blockchain intelligence firm to scrutinize wallet addresses left in ransomware notes that helped them trace the ransoms to Excoino, a cryptocurrency exchange based in Iran.
Putting the information together in a previous report, Check Point found that “an exceptional number of Israeli companies” reported ransomware attacks and that “several large corporations” experienced a full-blown attack with ransomware named Pay2Key. Upon analyzing Pay2Key, Check Point researchers were unable to correlate it to any other existing ransomware strain at that time. They had concluded that the ransomware was “developed from scratch.”
In its new report though, Check Point revealed that to date, “the non-paying victims” of this attack are “three Israeli companies.” It further stated:
The leaked data of each victim company was uploaded to a dedicated folder on the website, accompanied with a tailored message from the attackers. In the massage they share sensitive information regarding the digital assets of the victim, including details regarding their domain, servers and backups.
The researchers noted that the attackers used the same logo of the Pay2Key EOSIO smart contract system on Keybase to chat with their victims. However, the team believed this could have been a result of choosing the logo image at random from Google images:
Attackers behind the Pay2Key ransomware demand ransoms that range from about 7 to 9 BTC from their victims, and so far, four companies have decided to pay the hackers after their deposits were traced.
The post appeared first on AMBCrypto