According to a disclosure by Yearn Finance, a flash loan attack vector was discovered by a security researcher recently, before being resolved by Yearn’s security team.
A potential vulnerability was mitigated around 1.5 hours after being reported by Wen-Ding Li through Yearn’s security vulnerability disclosure process on 29 October 2020. It was also revealed that through the said flash loan vulnerability, funds of the TUSD vault could have been at risk. However, fortunately, it was not exploited and funds remained safe.
The security researcher who reported the attack disclosed that he had an initial proof of concept of a flash loan attack that could be mounted on the TUSD vault and could result in an 18% loss to users, with the attacker being able to walk away with 650K TUSD.
In an effort towards mitigation, the TUSD vault was soon configured to stop deploying funds to use its strategy while the problem was investigated and fixed.
Wen-Ding Li also pointed out that other vaults using the Curve strategy (such as the DAI vault and the GUSD vault) would potentially be vulnerable to the same attack. However, he did note that these vaults already have min set to zero and are therefore not as vulnerable.
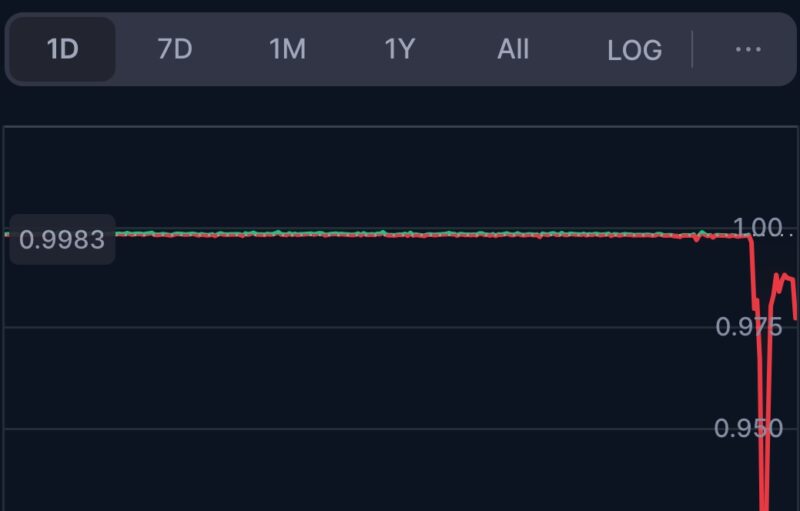
The disclosure came at an interesting time for many in the community since it followed not long after the recent incident with Harvest Finance. The said incident was also caused by a Flash Loan attack, one that leaves protocols helpless to the vulnerabilities in their code.
No hacker.Just a simple* $24M (0x53f) juicy arb on @harvest_finance
$50M USDC flash loan @UniswapProtocol
Swap $11M (USDC/USDT) @CurveFinance
~61M on fUSDT Vault
Swap $11M USDT/USDC yUSDT
Withdraw $61M with $0.5M profit
Repeat & clean into @TornadoCashhttps://t.co/nFTuyU3s6w pic.twitter.com/2oXQ2PsY32— Julien Bouteloup (@bneiluj) October 26, 2020
0. An unfortunate exploit has occurred in @harvest_finance . I took a look at the code, and there was one implementation bug and another design mistake.$FARM #harvest #exploit #bugs @ChrisBlec @Arthur_0x
— Pancake $Bunny on #BSC (@PancakeBunnyFin) October 26, 2020
Most developers that notice any potential issue in the code would choose to exploit it, but in this case, the vulnerability was reported and fixed quickly. Ergo, it can be said that Yearn Finance’s successful mitigation of the attack has highlighted how bounty programs for bringing attention to bugs such as this one are a success. However, there is a flip side to the same too, with the case yet another reminder of how vulnerable some of these projects are.
The post appeared first on AMBCrypto